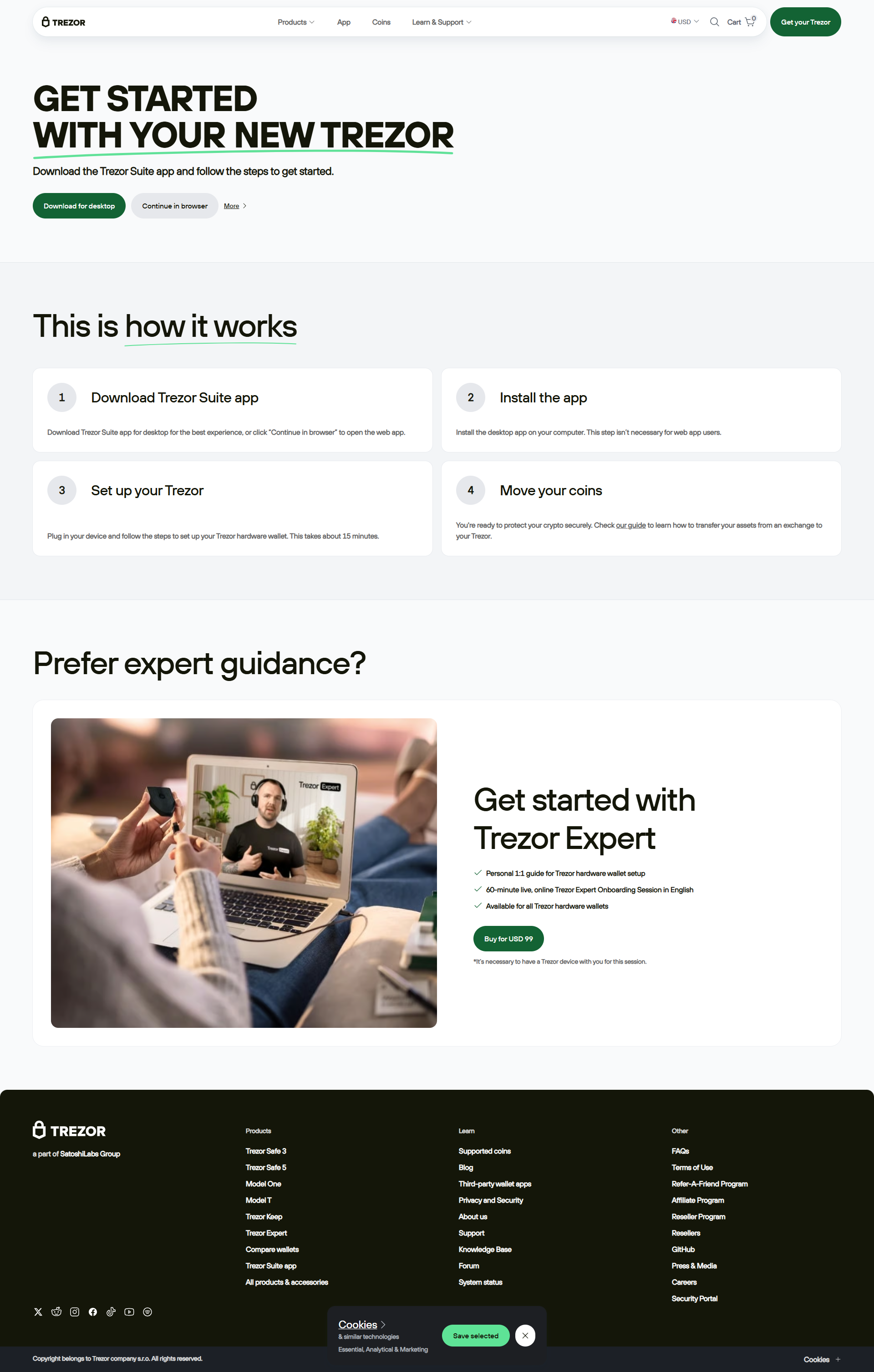
Trezor Login: The Modern Gateway to Digital Asset Security
Step-by-step insights into logging into your Trezor device, enhancing your crypto protection, and mastering secure self-custody.
🔐 What is Trezor Login?
Trezor Login is a hardware-based authentication method designed to protect cryptocurrency users from online threats. By using a physical device, Trezor ensures that your private keys never leave the hardware, keeping your funds immune from online hacking attempts. This system offers the highest level of crypto security through offline verification and human oversight.
💡 Core Philosophy
Trezor’s login philosophy centers around “ownership through autonomy.” It ensures no centralized exchange or platform controls your digital wealth.
🛡️ Ultimate Privacy
Your private keys remain offline, and all transaction verifications occur directly on the device’s screen—away from any potential digital surveillance.
⚙️ Simple Interface
The Trezor Suite dashboard simplifies crypto management with a clean layout, intuitive navigation, and built-in portfolio analytics.
🧭 Step-by-Step Trezor Login Process
- Step 1: Connect your Trezor wallet (Model T or One) using a USB cable.
- Step 2: Open Trezor Suite on your desktop or navigate to the official Trezor web portal.
- Step 3: Confirm that you’re on the legitimate trezor.io domain.
- Step 4: Enter your PIN using the randomized keypad displayed on your Trezor device.
- Step 5: Access your dashboard, review balances, manage accounts, and approve transactions securely.
⚖️ Trezor Login vs. Hot Wallets
| Feature | Trezor Login | Hot Wallets |
|---|---|---|
| Private Key Storage | Offline (Hardware) | Online (Cloud/App) |
| Risk of Hacking | Minimal | High |
| Accessibility | Requires Device | Immediate Access |
| Ideal For | Long-Term Investors | Active Traders |
💬 Expert Insight: Why Trezor Login Matters
Crypto veterans often emphasize the concept of self-custody. When you perform a Trezor Login, you exercise direct control over your private keys — no intermediary, no third-party server, and no risk of exchange failure. This decentralized authentication keeps your funds untouchable and your independence intact.
“Security in crypto isn’t about hiding your money; it’s about controlling your keys.”
🧰 Troubleshooting Trezor Login Issues
- Device not detected: Check USB cable and install the latest Trezor Bridge.
- PIN forgotten: Reset the wallet using your recovery seed to regain access.
- Phishing alert: Only log in from official sources; never share your recovery phrase.
- Firmware errors: Update firmware via Trezor Suite for the latest compatibility and security fixes.
📚 Frequently Asked Questions
1. Is Trezor Login necessary to view my wallet?
Yes. To view or manage funds, your Trezor device must be connected and authenticated through Trezor Suite.
2. What happens if I lose my device?
Your assets remain safe. Use your recovery seed to restore access on a new Trezor device.
3. Can Trezor Login be used with MetaMask?
Yes. You can integrate your Trezor with MetaMask for secure dApp and DeFi interactions.
4. How often should I update my firmware?
It’s recommended to check for updates every few months for new features and security enhancements.
Final Thoughts on Trezor Login
The Trezor Login process embodies the future of digital asset protection. By combining simplicity, transparency, and offline encryption, Trezor stands as the benchmark of crypto safety. Whether you’re holding Bitcoin, Ethereum, or DeFi tokens, every login reaffirms one core truth: you are your own bank.